Cyber Mesh Security Architecture
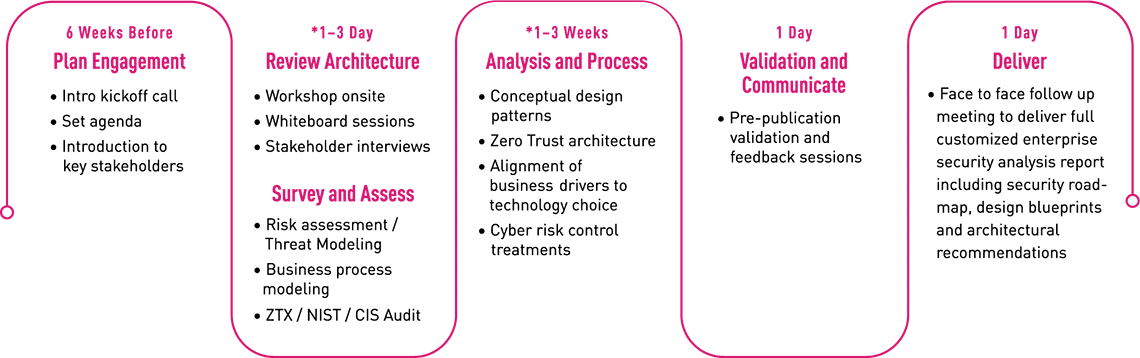
Enterprise Architecture Workshop
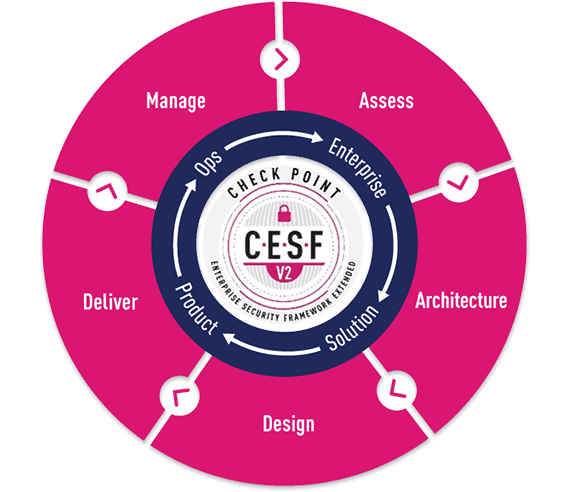
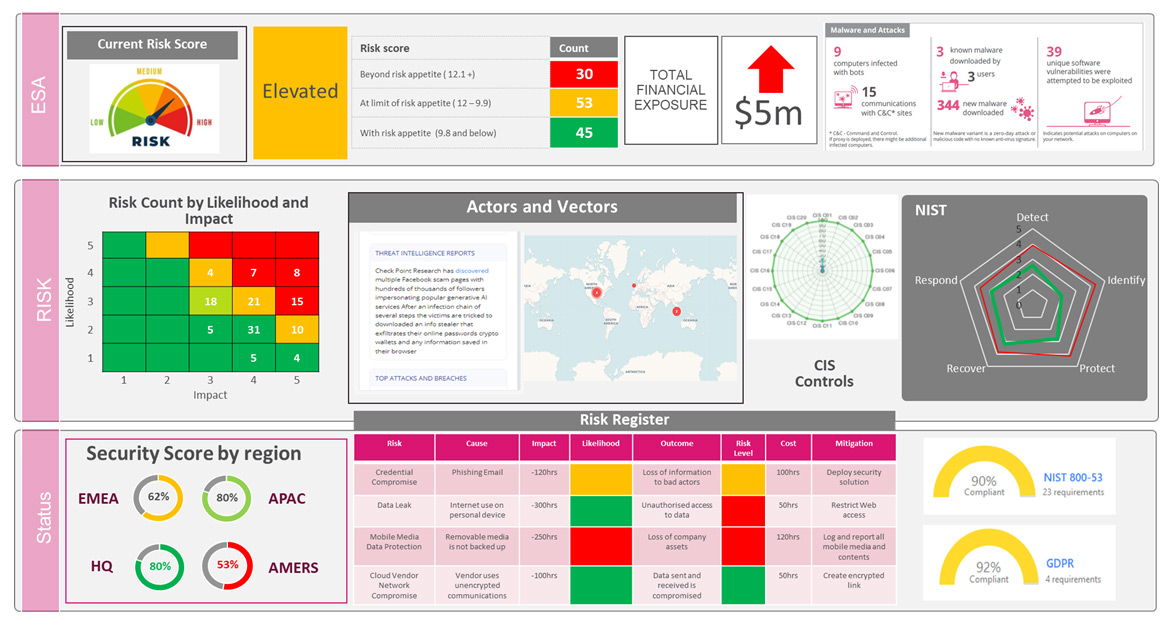
The Enterprise Security Architecture program provides a unique opportunity for organizations around the world to review their current and future security programs with Check Point’s most senior consultants. During these multi-day sessions the teams examine the organization’s business processes, security strategies, design, deployment and operational methods and compare these with industry and Check Point’s best practices. The outcome of the sessions is a customized security architecture intended to help ensure resilience to evolving attacks as well as optimized operational costs, consolidated controls and streamlined management, monitoring and maintenance practices.
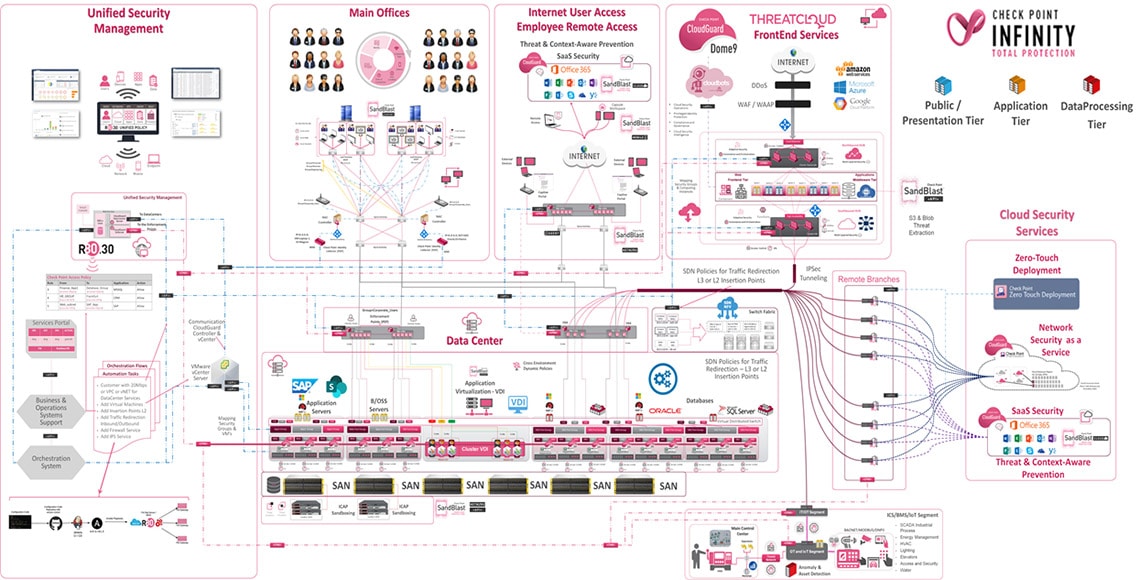
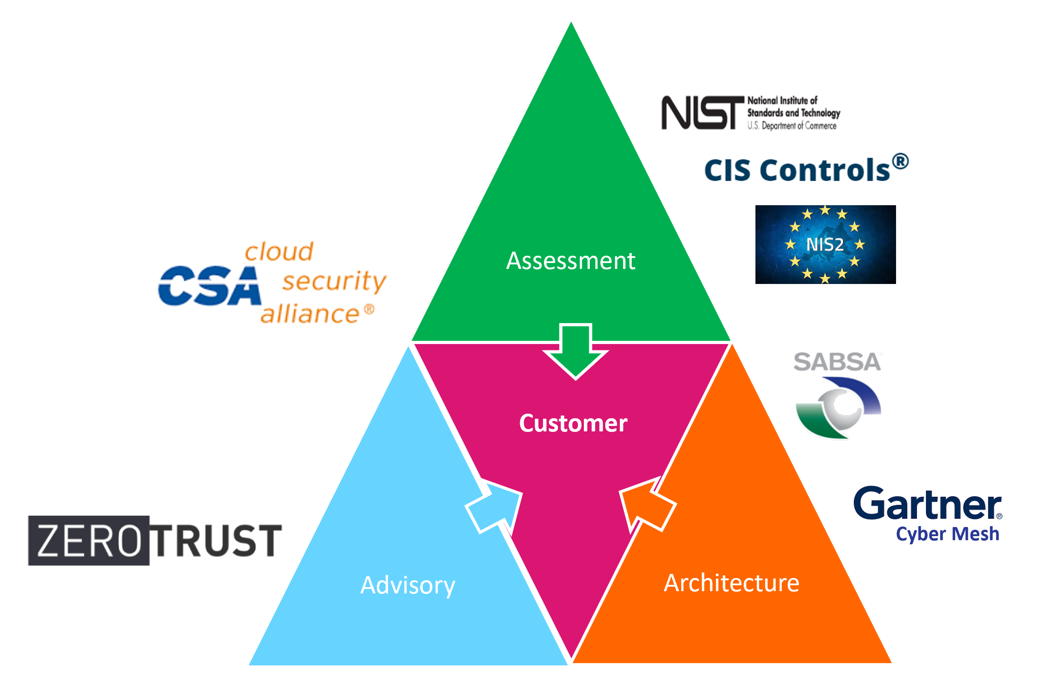
In the ever-evolving cybersecurity landscape, two prominent concepts stand out as game-changers in the industry: the “Cyber Security Mesh Architecture (created by Gartner) and the Zero-Trust Framework (by NIST-CISA and Forrester)”.
These approaches collectively empower organizations to fortify their digital environments against threats more effectively than traditional perimeter-based security models that are becoming less effective.
Check Point’s Strategic Consulting Team has found a relationship between the Zero-Trust Maturity Model and CSMA.
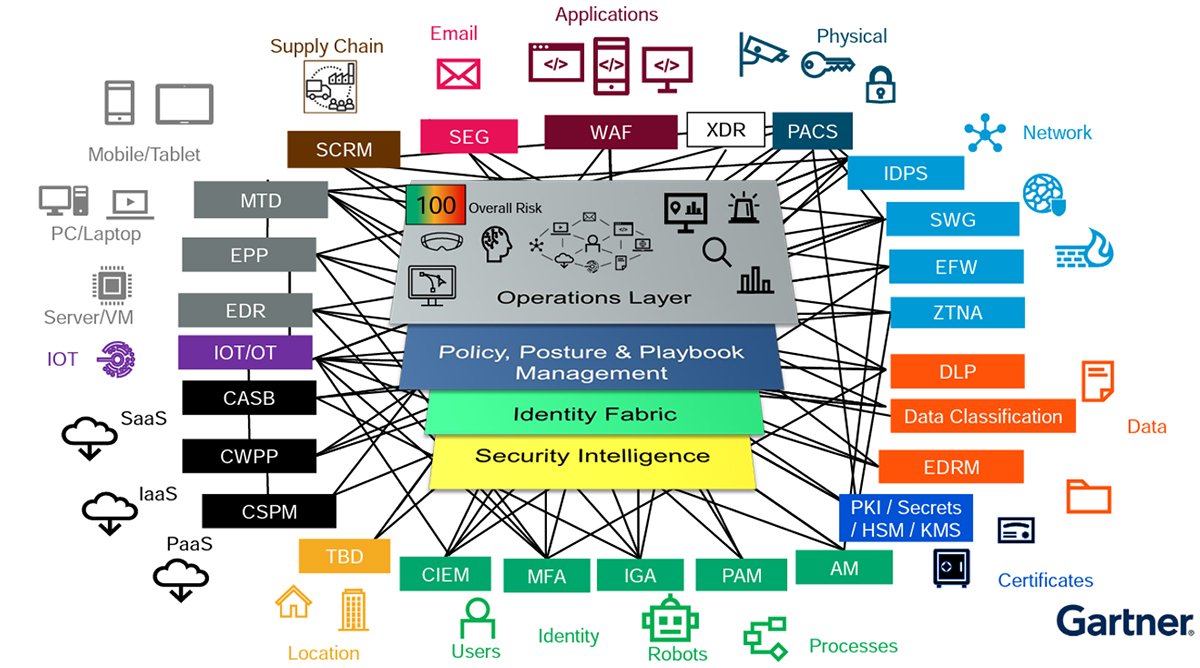
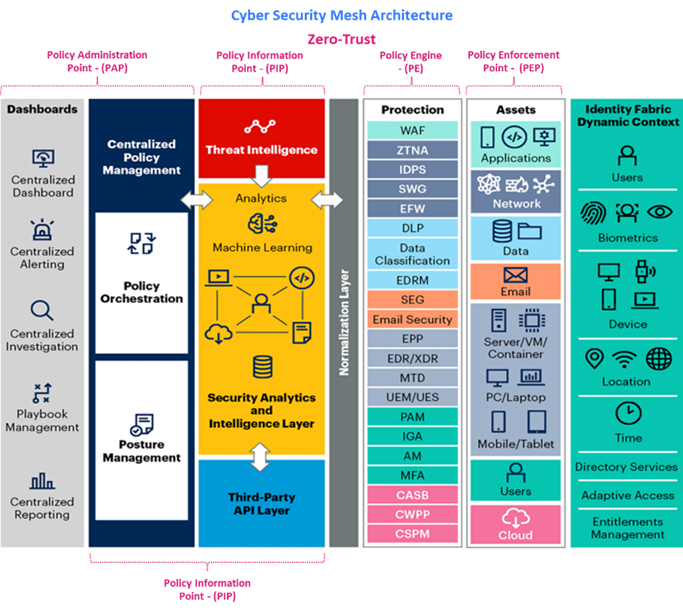
The Zero-Trust Maturity Model enables us to guide the strategic implementation of Zero-Trust principles.
At the same time, the Cyber Security Mesh Architecture operationalizes those principles by spreading security controls across the digital landscape.
Together, they provide a comprehensive approach to cybersecurity that promotes proactive risk management, continuous monitoring, and adaptive defense mechanisms, ultimately enhancing an organization’s ability to withstand and respond to evolving cyber threats.
“Information Security is a journey and not a destination.”
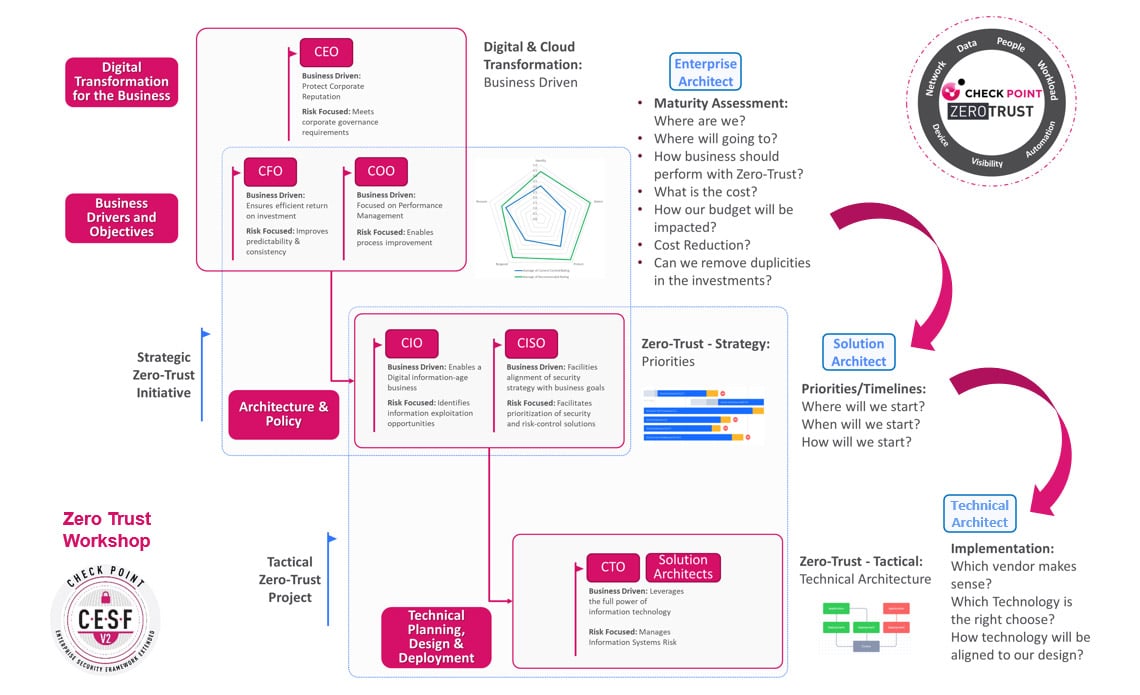
Our Consulting Services provide the CSMA and Zero Trust maturity assessment and advisory workshops, where our team will review your current readiness to appropriately define the priorities and roadmap implementation.
Our Consulting Services provide the CSMA and Zero Trust maturity assessment and advisory workshops, where our team will review your current readiness to appropriately define the priorities and roadmap implementation.
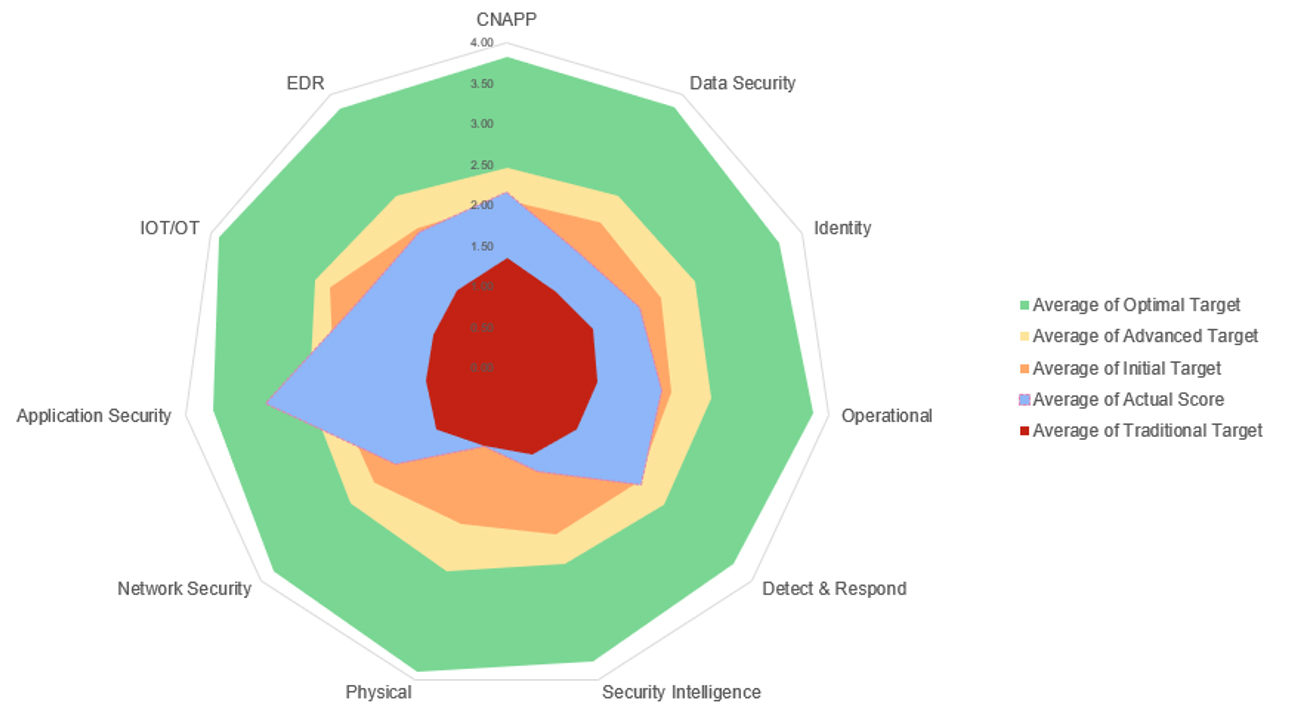
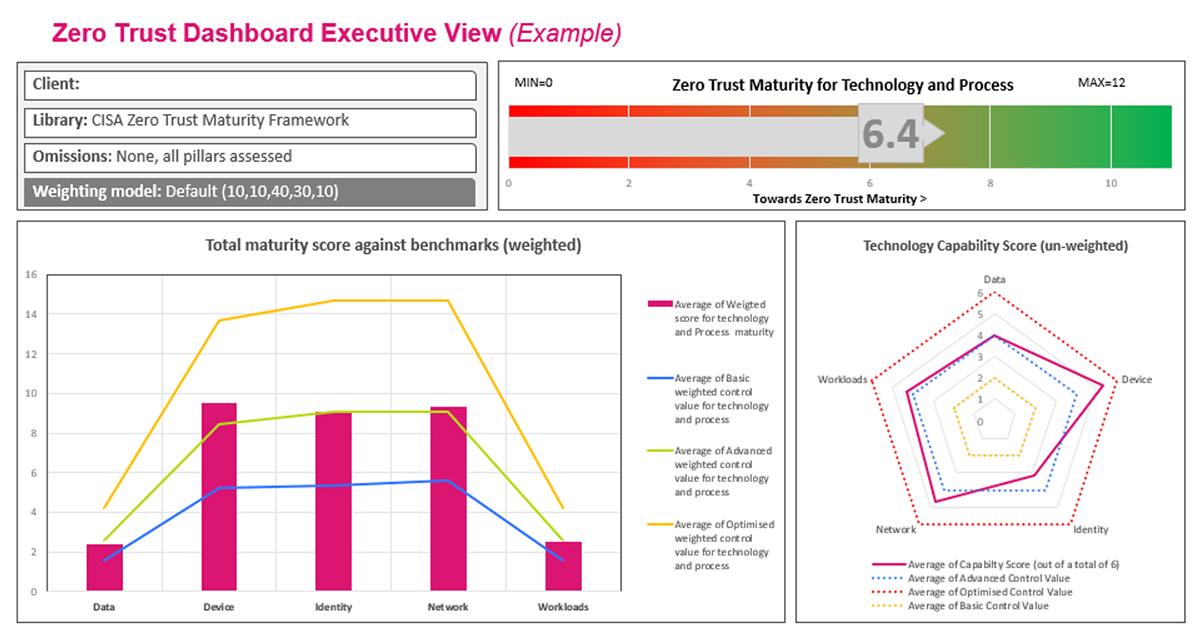
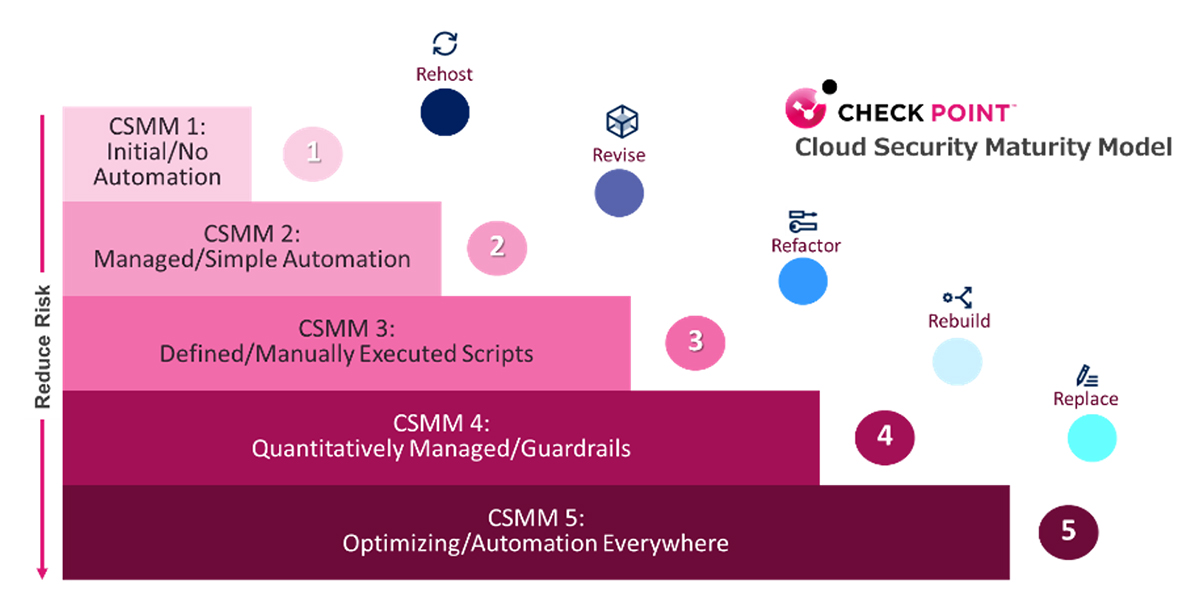
Our services can help you to evaluate your current Zero-Trust and CSMA maturity stage, validate the wins, and provide a prescriptive plan to help you take the next step successfully.
Benefits
- Identify the crown jewels: if you are just starting off, we will help you identify high-priority areas for protection.
- Assess your current state (AS-IS): we will review your existing identity, access the control environment, and policies to determine how they fit into a zero-trust framework.
- Visualize what’s next (TO-BE): we will help you to prioritize zero trust strategy and CSMA implementation milestones to align with business objectives.
- Plan the deployment: receive a detailed plan and roadmap with defined next steps for implementation readiness and actual deployment.
Contact our consulting team for help with your Zero-Trust Strategy and Cyber Security Mesh Architecture. We will assess your maturity level and guide your organization to ensure your organization’s safety and security.