 Our Zero-Trust Advisory Services are expertly crafted to empower organizations to create an unbeatable cybersecurity framework based on the principles of “least privilege with continuous verification” and “assume breach.” This approach is designed to secure your digital environment by meticulously validating every access request as if it originated from an open network, regardless of the user’s location or network segment.
Our Zero-Trust Advisory Services are expertly crafted to empower organizations to create an unbeatable cybersecurity framework based on the principles of “least privilege with continuous verification” and “assume breach.” This approach is designed to secure your digital environment by meticulously validating every access request as if it originated from an open network, regardless of the user’s location or network segment.
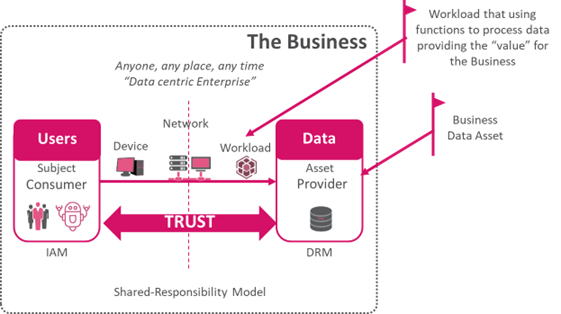 Zero-Trust framework enhances security posture and reduces attack surface. Our advisory services align security measures with industry standards, ensuring compliance and governance. Strictly monitored and controlled data access provides unparalleled protection. The framework is flexible, scalable, and future-proof. Eliminate outdated, redundant security layers to simplify protocols and reduce complexity.
Zero-Trust framework enhances security posture and reduces attack surface. Our advisory services align security measures with industry standards, ensuring compliance and governance. Strictly monitored and controlled data access provides unparalleled protection. The framework is flexible, scalable, and future-proof. Eliminate outdated, redundant security layers to simplify protocols and reduce complexity.

Benefits
Our team of seasoned experts will confidently guide you through the intricate process of implementing a tailored Zero-Trust Strategy that caters to your organization’s unique needs and security requirements with utmost confidence.
- Enhanced Security Posture: By adopting a Zero-Trust framework, your organization will significantly reduce the attack surface, making it more resilient against cyber threats.
- Regulatory Compliance: Our advisory services will help ensure that your security measures align with industry standards and regulations, aiding in compliance and governance.
- Zero Trust business value: Show how ZT framework aligns with the business and provide a value.
- Improved Data Protection: Zero-trust principles ensure that data access is strictly controlled and monitored, providing superior protection for sensitive information.
- Scalability: The framework is designed to be flexible, allowing it to grow and adapt to your organization.
- Reduced Complexity: Simplify your security protocols by eliminating outdated, complex, and redundant security layers.
CONTACT AN EXPERT
IGS PORTAL
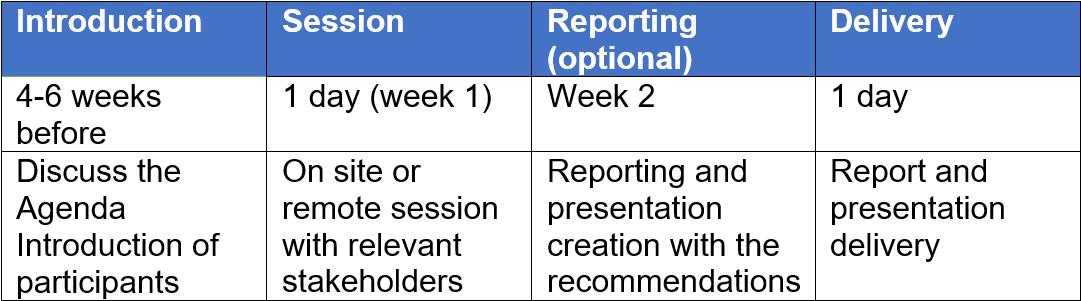
Delivery
With our unwavering commitment to excellence, you can rest assured that your digital assets will be thoroughly protected against any potential threats working with you on the following activities:
- Executive Summary: A concise report explaining the strategic implications and high-level recommendations for implementing a Zero-Trust framework. This document is designed to provide executives with a quick yet comprehensive understanding of the current state and the roadmap ahead.
- Strategic Roadmap: A visual and narrative representation of the phased approach towards achieving a Zero-Trust architecture. It outlines key milestones, resource allocation, and timelines, allowing executives to understand the journey immediately.
- Governance and Compliance Overview: A summary of how the Zero-Trust framework aligns with relevant industry regulations and governance standards, aiding executives in understanding the compliance landscape.
- Stakeholder Engagement Plan: A strategy for communicating and engaging with key organizational stakeholders to ensure buy-in and facilitate a smooth transition to a Zero-Trust model.
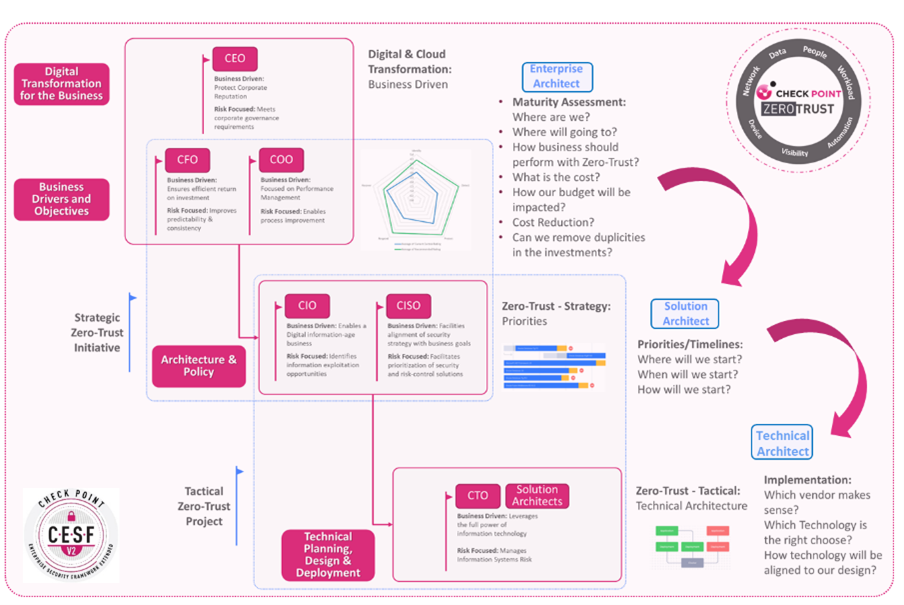

Most relevant roles
Key Stakeholders From Different Departments

Ideal number of participants
5-7 Professionals
Infinity Global Services
Check Point Infinity Global Services provides end-to-end security services that enables you to grow your team’s expertise, design best practices and prevent threats in real time. Wherever you are in your cybersecurity journey, we start there. Our elite experts will work together with your team to take your organization to the next level of protection and build your cyber resilience plan.






 Our Zero-Trust Advisory Services are expertly crafted to empower organizations to create an unbeatable cybersecurity framework based on the principles of “least privilege with continuous verification” and “assume breach.” This approach is designed to secure your digital environment by meticulously validating every access request as if it originated from an open network, regardless of the user’s location or network segment.
Our Zero-Trust Advisory Services are expertly crafted to empower organizations to create an unbeatable cybersecurity framework based on the principles of “least privilege with continuous verification” and “assume breach.” This approach is designed to secure your digital environment by meticulously validating every access request as if it originated from an open network, regardless of the user’s location or network segment.



