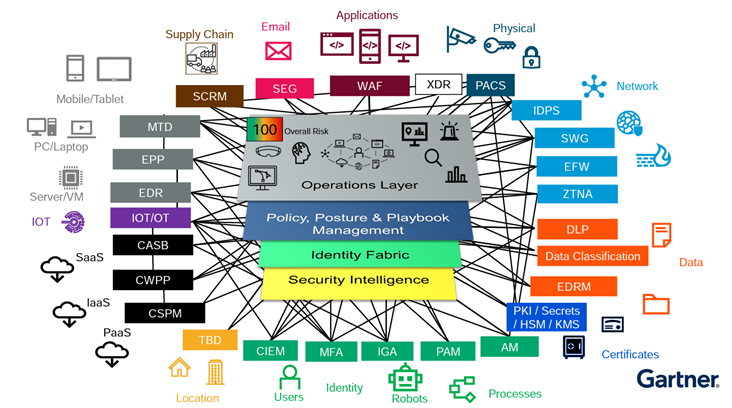
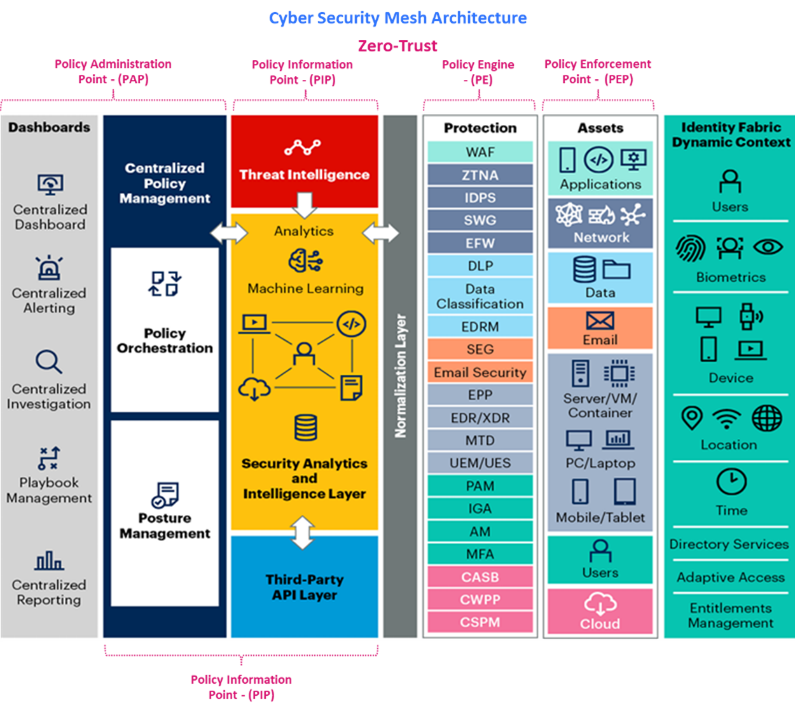
 In the ever-evolving cybersecurity landscape, two prominent concepts, the “Cyber Security Mesh Architecture (created by Gartner) and the Zero-Trust Framework (by NIST-CISA and Forrester),” stand out as game-changers in the industry. These approaches collectively empower organizations to fortify their digital environments against threats more effectively than traditional perimeter-based security models that are becoming less effective.
In the ever-evolving cybersecurity landscape, two prominent concepts, the “Cyber Security Mesh Architecture (created by Gartner) and the Zero-Trust Framework (by NIST-CISA and Forrester),” stand out as game-changers in the industry. These approaches collectively empower organizations to fortify their digital environments against threats more effectively than traditional perimeter-based security models that are becoming less effective.
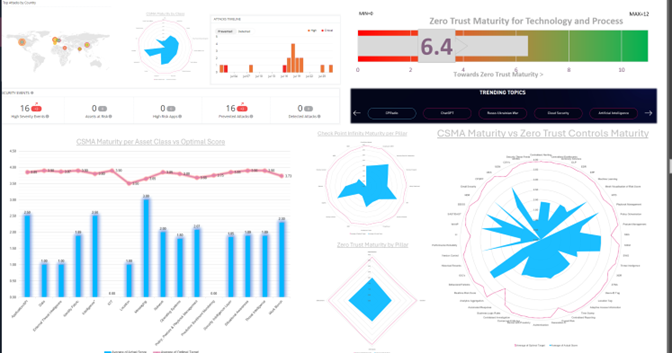
Check Point strategic consulting team has found a relationship between the Zero-Trust Maturity Model and CSMA.
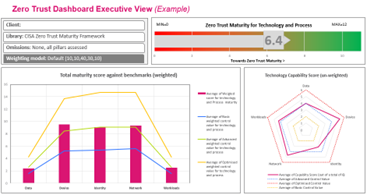
 The Zero-Trust Maturity Model enables us to guide the strategic implementation of Zero-Trust principles.
The Zero-Trust Maturity Model enables us to guide the strategic implementation of Zero-Trust principles.
At the same time, the Cyber Security Mesh Architecture operationalizes those principles by spreading security controls across the digital landscape.
Together, they provide a comprehensive approach to cybersecurity that promotes proactive risk management, continuous monitoring, and adaptive defense mechanisms, ultimately enhancing an organization’s ability to withstand and respond to evolving cyber threats.
“Information Security is a journey and not a destination.”
Our Consulting services provide the CSMA and Zero Trust maturity assessment and advisory workshops, where our team will review your current readiness to define appropriately the priorities and roadmap implementation.
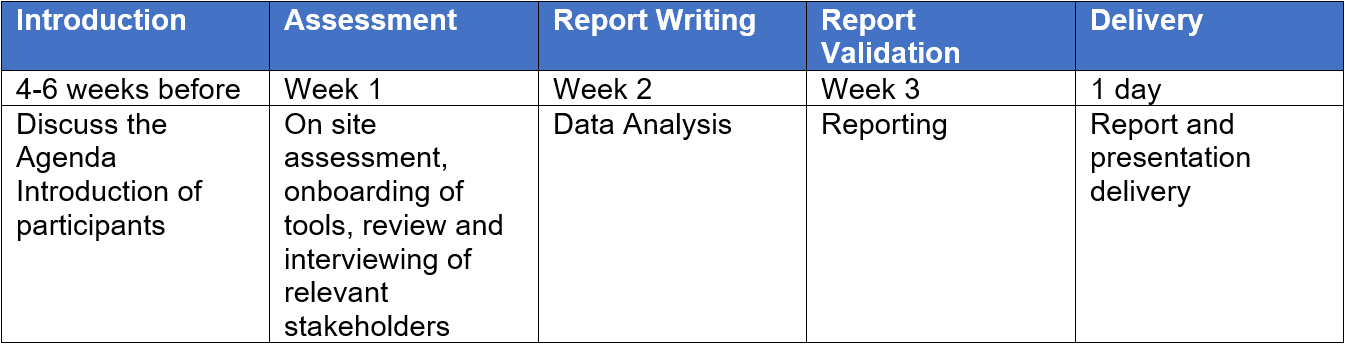
Delivery
The Check Point team prepares for success with in-depth engagement planning, up to six weeks in advance of our onsite time. With a firm plan in hand, we’ll spend one to three (1-3) days onsite, working with you to review and assess your environment.
Post-visit, our experts will analyze findings and present recommendations. The timeline for the report may vary, with completion typically expected within up to four (4) weeks, contingent on the assessment’s outcomes.

Most relevant roles
Key Stakeholders From Different Departments

Ideal number of participants
2-5 Professionals
Infinity Global Services
Check Point Infinity Global Services provides end-to-end security services that enables you to grow your team’s expertise, design best practices and prevent threats in real time. Wherever you are in your cybersecurity journey, we start there. Our elite experts will work together with your team to take your organization to the next level of protection and build your cyber resilience plan.