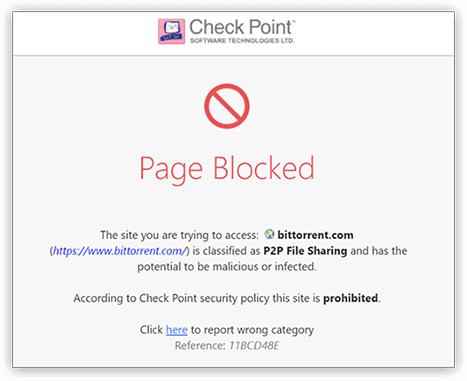
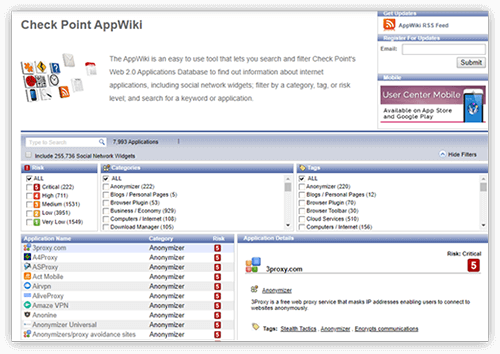
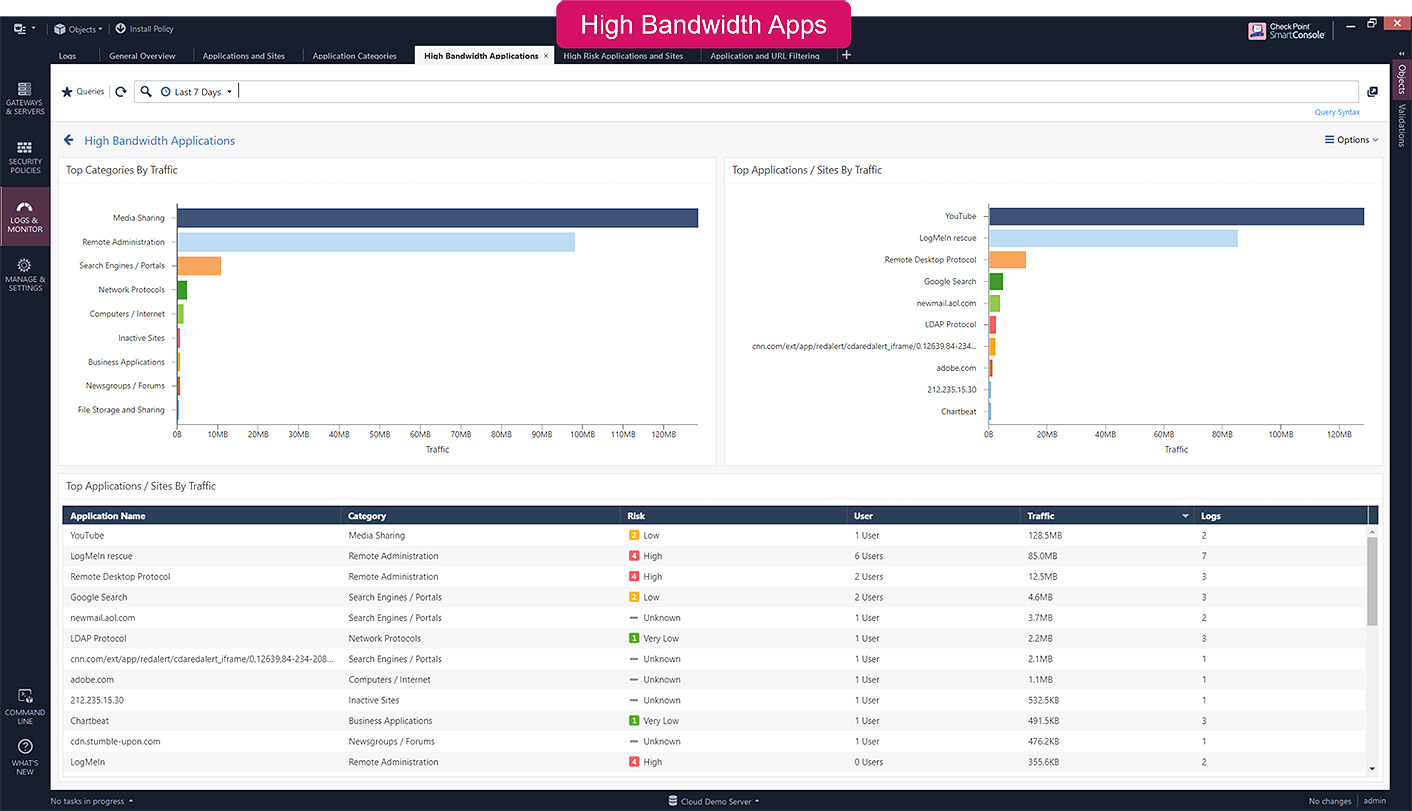
-
Search
- Geo Menu
-
Products
- Network & SASE
- Cloud & Applications
- Security Operations
- AI
-
Solutions
Use CasesIndustryBusiness Size
-
Products
- Network
- SASE
- Cloud
- Workspace
- Security Operations
- AI
-
Solutions
- Use Cases
- Industry
- Organization Size
-
Platform
-

2025 Cyber Security Report
DOWNLOAD REPORT
- Services
-
Resources
-

2025 Cyber Security Report
DOWNLOAD REPORT
-
Partners
-

Check Point is 100% Channel. Grow Your Business with Us!
Sign Up Now
-
About Us
-

Nadav Zafrir Named New
Learn More
Check Point CEO