Manage and Mitigate External Cyber Risks
Elevate your security operations with an external risk management solution that protects against threats like credential theft, fraud, and brand impersonation.

GigaOm Names Infinity External Risk Management as a Market Leader in Attack Surface Management
Continuously Mitigate Threats Across the Web
Threat intelligence, digital risk protection, external attack surface management, dark web monitoring, and supply chain risk mitigation
- Continuous Protection and Remediation
Advanced technologies monitor the web, analyze vast sums of data, and correlate threat intelligence with your assets. - Comprehensive Cyber Risk Mitigation
Detect and mitigate numerous risks, from misconfigurations and CVEs to phishing attacks, exposed credentials, and data leaks. - Quantified External Risk Reduction
Quantify your organization’s external cyber risks, measure risk reduction over time, and easily report on progress to executive leadership.
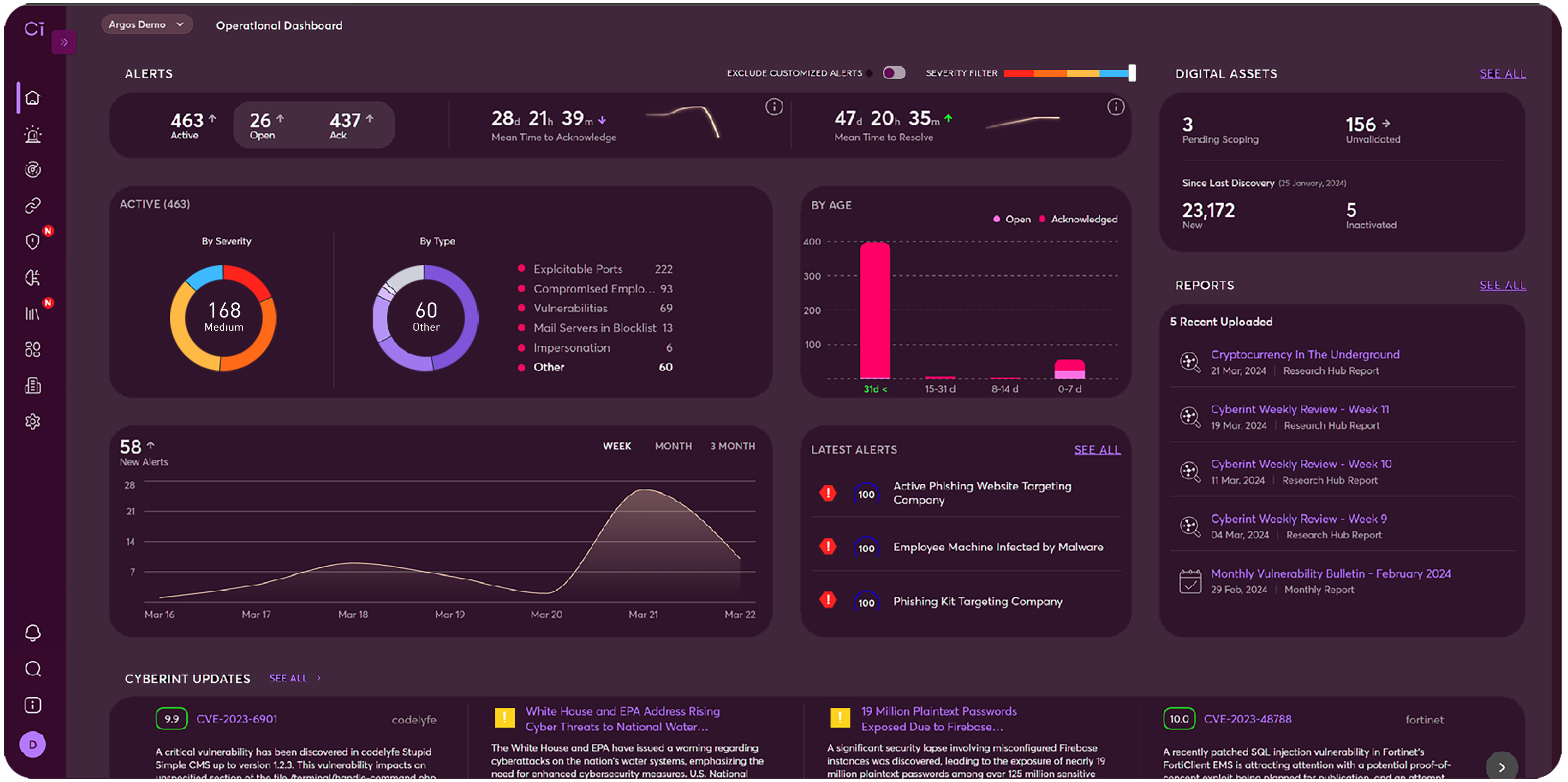
See Infinity External Risk Management in Action.
Extensive Capabilities in a Single Solution
We provide a comprehensive suite of capabilities to protect your organization from external cyber risks.
Attack Surface Management
Continuously discover, assess, and protect your organization’s internet-facing assets.
Digital Risk Protection
Detect and take down attacks that impersonate your organization’s brands or executives.
Cyber Threat Intelligence
Access a library of strategic intelligence, conduct forensic investigations, and operationalize threat intelligence.
Supply Chain Intelligence
Evaluate, monitor, and manage external risks introduced through your third-party suppliers and vendors.
Deep and Dark Web Monitoring
Gain exclusive visibility into thousands of sources across the deep and dark web to detect targeted threats.
Quantified Risk Scoring and Reporting
Measure, monitor, and report on your organization’s external cyber risk to demonstrate quantified progress and value.
Explore Infinity External Risk Management.
See External Risk Management in Action
- Attack surface Management
- Cyber Threat Intelligence
- Digital Risk Protection
- Supply Chain Intelligence
End-To-End Protection Against External Cyber Risk
Check Point Infinity External Risk Management allows you to replace siloed products with a comprehensive solution that mitigates many external risks simultaneously.
Defend Attack Surface
Map out your digital estate, create an asset inventory, identify exposures, assess risks, and prioritize issues for rapid remediation – automatically and continuously.
Protect Brand Assets
Detect attacks that impersonate your brand, such as phishing sites, fraudulent social media profiles, malicious applications, and more.
Monitor the Deep and Dark Web
Gain unparalleled visibility into thousands of sources across the deep and dark web to uncover hidden threats targeting you.
See Infinity External Risk Management in Action.
Explore External Risk Management Resources

Infinity External Risk Management Solution Brief
Check Point Infinity External Risk Management provides continuous and comprehensive protection against external cyber threats.
 Phishing & Impersonation Protection Handbook
Phishing & Impersonation Protection Handbook
Phishing and other brand impersonation attacks are a tried-and-true technique for threat actors. Learn more about these attacks and how you can prevent them.
 Managing Cyber Risk Exposure
Managing Cyber Risk Exposure
Quantifying cyber risk is no easy task. How should cyber leaders make decisions when there is so much uncertainty? Learn more in this ebook.
 Raising The Stakes For Attack Surface Management
Raising The Stakes For Attack Surface Management
The attack surface is often defined narrowly, overlooking many common methods and techniques. Learn how to defend your full attack surface here.
 The Big Book Of Deep & Dark Web
The Big Book Of Deep & Dark Web
To many cyber defenders, the deep and dark web remains a mystery. Learn more about the types of threats lurking on the dark web and how to mitigate them.
Our Customers Love Us
Explore how Check Point’s global customers are safeguarding their environments. Our mission is to secure the digital landscape for all, everywhere, with cutting-edge security solutions. We proudly maintain an industry-leading prevention rate of 99.8%.