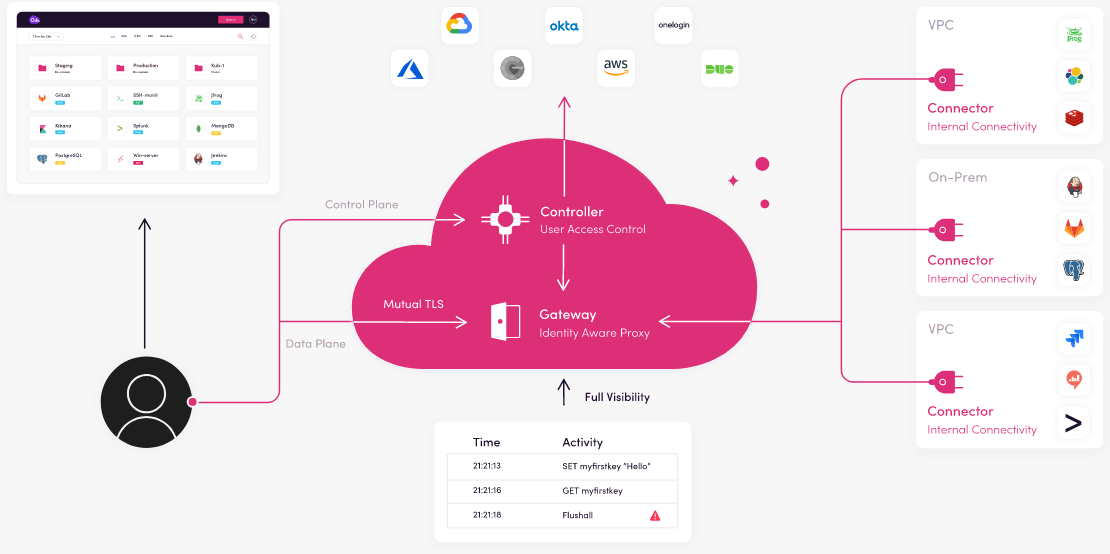
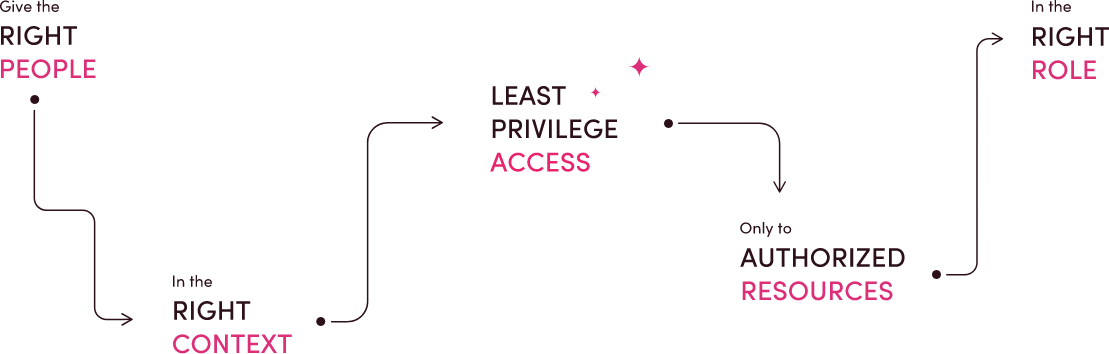
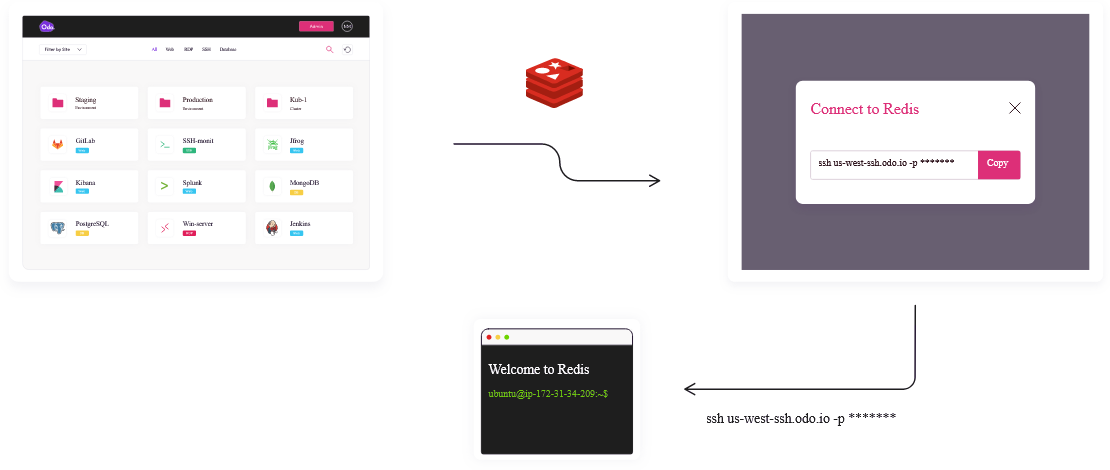
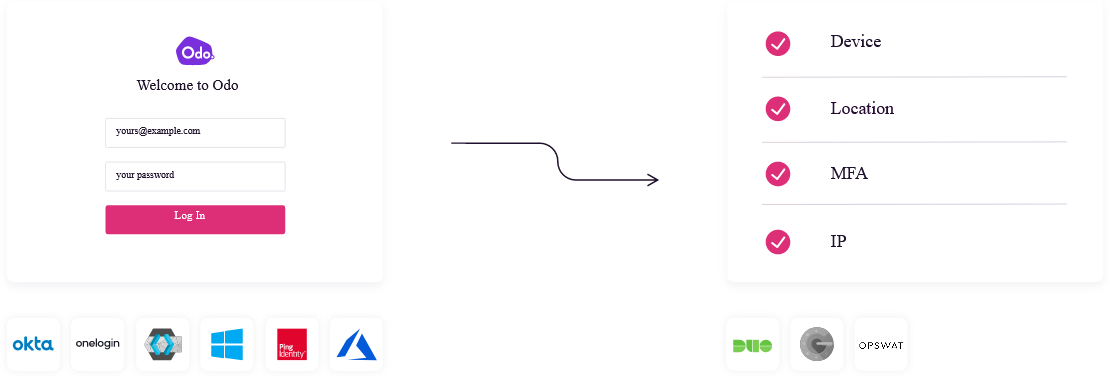
-
검색
- 지역 메뉴
-
솔루션
-

Unveiling the Future of Network Security in the Era of AI
Watch The Replay -

Unveiling the Future of Network Security in the Era of AI
Watch The Replay -

Unveiling the Future of Network Security in the Era of AI
Watch The Replay
-
플랫폼
- 인피니티 살펴보기
-

Unveiling the Future of Network Security in the Era of AI
Watch The Replay -
Quantum 살펴보기
- NGFW(차세대 방화벽) 보안 게이트웨이현대 기업을 위한 업계 최고의 AI 기반 보안 게이트웨이
- SD-WAN소프트웨어 정의 와이드는 보안과 네트워킹을 통합하는 네트워크
- 보안 정책 및 위협 관리온프레미스 및 클라우드 네트워크를 위한 통합 플랫폼에서 방화벽 및 보안 정책 관리
- 사물인터넷(IoT) (IoT)Autonomous IoT threat prevention with zero trust profiling, virtual patching, and segmentation
- 원격 액세스 VPN 기업 네트워크에 대한 안전하고 원활한 원격 액세스
- Industrial Control System Security Gateways ICS, 운영 기술 및 SCADA 시스템 보호
- 모든 제품 보기 >
-

Unveiling the Future of Network Security in the Era of AI
Watch The Replay - CloudGuard 살펴보기
-

Unveiling the Future of Network Security in the Era of AI
Watch The Replay - Harmony 살펴보기
-

Unveiling the Future of Network Security in the Era of AI
Watch The Replay -
Security Operations
- External Risk ManagementProtect against threats like credential theft, fraud, and brand impersonation.
- 확장형 차단 및 대응인피니티 XDR/XR을 통한 AI 기반의 클라우드 제공 보안 운영
- 안전한 자동화 및 협업인피니티 Playblocks로 대응 플레이북 자동화
- 서비스형 통합 보안 이벤트 및 로그인피니티 이벤트 클라우드 기반 분석, 모니터링, 보고
- AI 기반 팀메이트자동화된 보안 관리자 및 AI Copilot을 통한 사고 대응
- ThreatCloud AI체크포인트 최고의 위협 차단을 뒷받침하는 두뇌
- 관리형 예방 및 대응 서비스인피니티 MDR/MPR을 통한 SOC의 서비스형 운영 제공
- GenAI ProtectDiscover GenAI apps, assess their risk, and prevent data loss
- 모든 제품 보기 >
-

Unveiling the Future of Network Security in the Era of AI
Watch The Replay
-
지원 및 서비스
-
전략 & 위험 서비스 살펴보기
- External Risk ManagementOutsource specialized cybersecurity functions to Check Point security experts
- 사이버 위험 평가사이버 위험을 평가하고 실행 가능한 전략 수립
- 공격 표면 및 침투 테스트잠재적 사이버 공격 및 위협에 대한 보안 방어 평가
- 보안 제어 격차 분석
(NIST, CIS)기술 격차를 분석하고 보안 및 ROI 향상을 위한 솔루션 계획 - 위협 인텔리전스 및 브랜드 평판사이버 위협에 대한 데이터를 분석하여 사전 예방적 보안 조치 지원
- 모든 전략 & 위험 서비스 보기 >
-

인피니티 Global 서비스
모든 서비스 살펴보기
조직의 특정 요구 사항을 충족하기에 적합한 엔드투엔드 사이버 보안 서비스 솔루션을 찾아보세요. - 프로페셔널 서비스 살펴보기
-

인피니티 Global 서비스
모든 서비스 살펴보기
조직의 특정 요구 사항을 충족하기에 적합한 엔드투엔드 사이버 보안 서비스 솔루션을 찾아보세요. - 교육 프로그램 살펴보기
-

인피니티 Global 서비스
모든 서비스 살펴보기
조직의 특정 요구 사항을 충족하기에 적합한 엔드투엔드 사이버 보안 서비스 솔루션을 찾아보세요. - 사고 대응 서비스 살펴보기
-

인피니티 Global 서비스
모든 서비스 살펴보기
조직의 특정 요구 사항을 충족하기에 적합한 엔드투엔드 사이버 보안 서비스 솔루션을 찾아보세요. - 관리형 보안 서비스 살펴보기
-

인피니티 Global 서비스
모든 서비스 살펴보기
조직의 특정 요구 사항을 충족하기에 적합한 엔드투엔드 사이버 보안 서비스 솔루션을 찾아보세요. - 지원 서비스 살펴보기
-

고객 지원팀은 클릭 한 번으로 24시간 언제든지 도움을 드릴 준비가 되어 있습니다.
지원 센터 방문
- 솔루션
-
플랫폼
- 인피니티 플랫폼
- 네트워크 보안
- 클라우드 보안
- 작업 공간 보안
- Security Operations
-
지원 및 서비스
- 전략 & 위험
- 프로페셔널 서비스
- 교육 프로그램
- 인시던트 대응
- 관리형 보안
- 지원
- 파트너
-
기타
- 회사
- 학습
- 사이버 보안 통찰력
-

Unveiling the Future of Network Security in the Era of AI
Watch The Replay