Secure the Network
Quantum Security Gateways Keep the Perimeter Secure
Check Point’s Quantum line of security gateways are time-tested to prevent today’s fifth generation of cyber attacks. A critical component of the Infinity Architecture, Quantum solutions protect enterprise networks, data centers, and IoT networks and devices.

LEARN MORE
Secure the Cloud
CloudGuard Cloud Native Security, Automated Everywhere
Check Point CloudGuard provides unified, cloud native security for all your assets and workloads, giving you the confidence to automate security, prevent threats, and manage posture – everywhere across your multi-cloud environment.
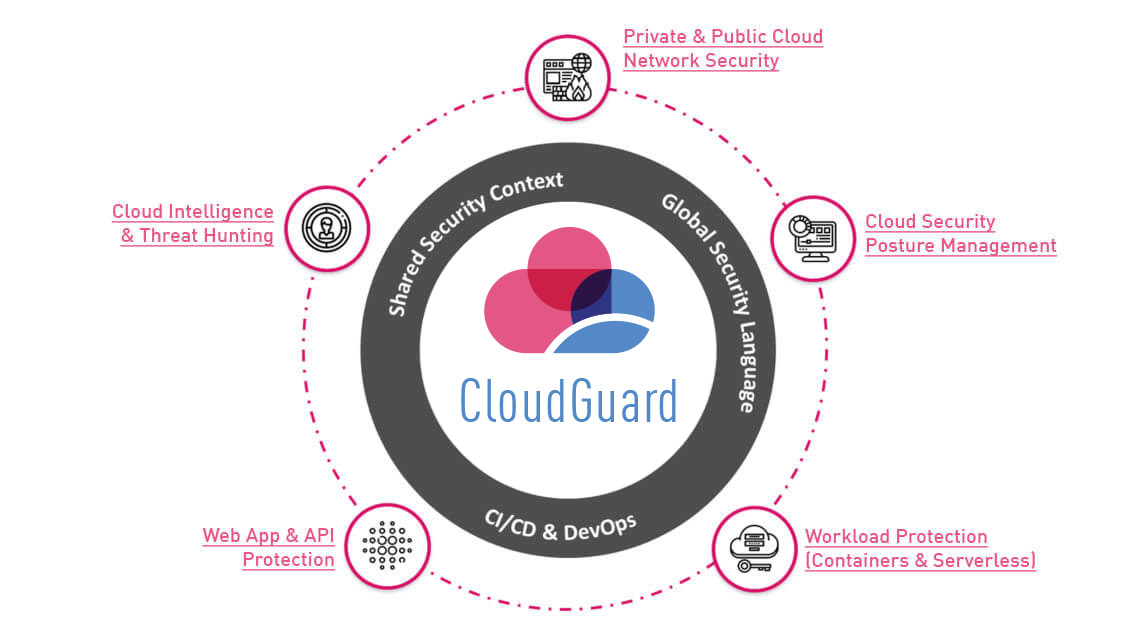
LEARN MORE
Secure Users and Access
Complete Protection for Users and Access
Check Point Harmony provides multi-layered and holistic security to protect remote users, access, applications, and data across all attack vectors.

LEARN MORE























